| Top 5 Benefits of Smart City Asset Management for Cyber Security |
|---|
| 1. Reduced risks and threats associated with the management of assets – including downtime, unnecessary maintenance and lack of availability |
| 2. Improved security assurance for businesses/citizens – where City assets play a key role in the provision and quality of products and services and data integrity |
| 3. Increased configuration management to ensure timely patch management and software updates |
| 4. Asset classification to enhance identification and association |
| 5. Asset ownership to aid departmental management and operational roles and responsibilities |

The categorisation, classification and maintenance of cyber-physical assets and systems essential to the administration, productivity and success of a Smart City.
How to use this Design Pattern:
A Business or Organisation Design Pattern is guide or blueprint for the development of a service or system through the specification of an architecture and plan. It should reference and be guided by best practice and appropriate standards to evidence the effectiveness and success in implementation. Cyber Security is dependant upon City Asset Management and not responsible for it and so must work with the appropriate departments to define requirements and approach to engineer the necessary solutions. The purpose of this design guide is to help those responsible for cyber security define the integration with existing City Asset Management services, that may or may not have to evolve and improve, to meet the future cyber security needs of the City. This design pattern is set out over ten steps:-
Step 1 – Identify the Capability needed to meet the objectives for the selected Strategic Option(s)
Step 2 – Define the use cases and criteria for the required Capability
Step 3 – Align standards and regulation requirements
Step 4 – Model the Capability domain
Step 5 – Define Actors, Roles and Responsibilities
Step 6 – Define the solution and technologies
Step 7 – Define the service requirements
Step 8 – Define the Target Operating Model and supporting Views
Step 9 – Deliver the strategy through a Transformation Plan
Step 10 – Monitor in-life Change, Performance and Maturity development
Strategic Findings:
1, Individual Departments responsible for own Asset Management
2, Asset Management classification out of date
3, Cyber Security unable to account for large percentage of City Assets connected to the Internet.
4, Cyber Security unable to collect and analyse City Asset data.
Strategic Options:-
1, Conduct audit and assessment of current asset management capability
2, Outline new cyber security requirements and assess audit findings
3. Implement new city wide Asset Management System and classification
4. Consolidate existing data and implement new systems or improvements where gaps exist.
5, Implement quarterly audit of all Asset Management processes and change controls
| Source | Public Domain References |
|---|---|
| City of New Westminster, British Columbia, Canada | Asset Management, Asset Management Policy |
| City of Calgary, Alberta, Canada | Asset Management Department, Asset Management Status Report |
| City of Winnipeg, Manitoba, Canada | Asset Management Department reports |
Overview
Smart City Asset Management is a source of Context and Reference Data to support critical security operations and protective monitoring capabilities. It requires a a governance role at a City Executive level and responsibilities to be shared across the different departments and technology service management. Classification of Smart Asset types is necessary to determine risk and impact assessments and the registry and management of the City Assets must be audited regularly and the timeliness and accuracy performance measured. As normally non-IT assets become smart and connected City Asset Management requires greater integration between City Departments and the ICT Departments to better define new smart Asset types. City Security Operations need to know specific properties of different asset types or systems controlling assets so that necessary data can be logged or events monitored. Asset management is a fundamental requirement of situational awareness so that the security state and health of a City can be monitored 24*7 and every day of the year.
These are the strategic use cases necessary for the development of this Function and the different city or security operations capabilities required to fulfil them. It is anticipated that asset management, to some degree of formality, already exists in many of the City’s Administration and Organisation departments e.g. Housing, Street & Road Management, Citizen Registries, Commercial and IT. Primarily, asset management has been to manage the maintenance, repairs, configurations and updates to city assets, now this role will include a responsibility towards the cyber-physical security and monitoring of evolving and new assets. Challenges will include:-
| 1, Agreeing and defining “Smart Assets and Services” 2, Ownership and responsibility of assets 3, Asset technologies and communication 4, The assessment and audit of City-wide asset management and systems maturity 5, Asset categorisation and classification 6, Integration of asset registries or the development of a new asset management system |
Categorisation
It is likely that Asset Management is already in operation across many of the different departments and services within the City Administration and Third Party Services. This is likely to cover ICT, Land, Buildings, Housing, Transportation and Infrastructure and may or may not be centrally managed. Existing City Asset categories should be reviewed to determine how suitable they are to support new requirements and be amended or updated with new asset types.
Classification
Each of the asset categories across the different City departments and services will require some specific classification particular to their purpose and use. There are a growing number of classification models and standards advising on classification types. The Asset Management of Connected Assets within Smart Cities will become increasing more important as more and more assets and services interact. Asset classification will be used to determine key risk and threat factors as well as impact and implications of loss of availability or integrity.
Design Use Cases to help align standards and compliance
The range of cyber security standards and regulations available provide a combination of guidance, best practice, dependencies and principles to help define and support the capabilities. Individual City departments may have other standards and compliance associated with Asset Management that is particular to the Assets they govern and maintain. I will attempt to research these and add any i find.
In many cases, much of the criteria for a security capability can come from standards and best practice. They may not be specific to smart cities as yet but they have been developed and refined over recent years and the instruction is very valid. Implementing part or all of a standard my increase the effectiveness and maturity of a capability. This is particularly important for the key Detect and React capabilities. Regulations for Smart Cities and various Smart Services may well come into force as defined by individual Governments as well as Standards that City Administrators will need to consider how they direct cyber security services.
Cyber Security and Asset Management Use Cases
ISO 55000 is an international standard covering management of assets of any kind. source Wikipedia
Organization and digitization of information about buildings and civil engineering works, including building information modelling (BIM). Information management using building information modelling. Source BSI
Specification for information management for the operational phase of assets using building information modelling. Source BSI
ww 1192-5:2015
Specification for security-minded building information modelling, digital built environments and smart asset management. Source BSI
Use Case 1 – Physical assets and devices within the City are inventoried. Guidance can be obtained from:-
- COBIT BAI03.04, BAI09.01, BAI09, BAI09.05
- ISO/IEC 27001 A.7.1.1, A.7.1.2
- CIS Control 1
Use Case 2 – Software platforms and applications within the City are inventoried. Guidance can be obtained from:-
- COBIT BAI03.04, BAI09.01, BAI09, BAI09.05
- ISO/IEC 27001 A.7.1.1, A.7.1.2
- CIS Control 2
Use Case 3 – City communication and data flows are mapped. Guidance can be obtained from:-
- COBIT DSS05.02
- ISO/IEC 27001 A.7.1.1
- CIS Control 1
Use Case 4 – External information systems are catalogued. Guidance can be obtained from:-
- NIST SP 500-291 3, 4
Use Case 5 – City Resources are prioritised based on their classification, criticality, and business value. Guidance can be obtained from:-
- COBIT APO03.03, APO03.04, BAI09.02
- ISO/IEC 27001 A.7.2.1
Use Case 6 – Cybersecurity roles and responsibilities for the City workforce and within third-parties are established. Guidance can be obtained from:-
- COBIT APO01.02, BAI01.12, DSS06.03
- ISO/IEC 27001 A.8.1.1
Use Case 3 City communication and data flows audit and assessment tool.
The Art of Service has a guide to Data Flow assessment and auditing. The list below is a selection of example questions.
- If a breach occurs or the regulator investigates the organisation; you need to have documents to explain the complete data flows. Are you ready to answer those questions as the level of fines will take into account the processes; technology; and documentation that describes the systems and flow of data. Are you ready for that?
- What is a standard data flow, and what should be the source and destination of the identified data?
- A baseline of network operations and expected data flows for users and systems is established and managed?
- Data Flow; what are the files and fields that are input, how are they transformed, how are they output?
- What restrictions are given by the IT-infrastructure regarding data flow and data utilisation?
- How do you identify a data flow, especially in different layers of the storage system?
Capability Model and Criteria
The example Capability Criteria taxonomy below guides the types of characteristics needed to detail a high-level view of the required capability. A lower level of Criteria will need to extend this high level set with the attributes needed to address specific Smart City technologies, services and new functions. The lower level attributes should encompass terminology derived from the emerging Smart City controlled vocabularies and related taxonomic structures. This ensures a level of consistency across all the capabilities and will aid integration and interoperability.
Summary
Asset Management shall ensure a quality of management necessary to oversee all feasible city assets capable, currently or in the future, of technology functionality and connectivity.
Directive
- To ensure Asset Inventory
- Existence of ownership of Assets
- Existence of support, warranty and recording of updates
- Existence of definitions of functionality, configuration and acceptable use
- Existence of Asset categorisation and classification
- Existence of maintenance and decommissioning
Governance
- City Executive
- Asset Management per Department
- City CISO
- City CTO
- City IOT Strategy Planning
- City Cyber Security
Technologies
- Legacy systems
- Cloud Services
- Commercial Off-The-Shelf solution
- IBM Product map to NIST CSF
- Microsoft Product map to NIST CSF
Roles
- City Executive
- City CISO
- Departmental Asset Management
- Asset Management Team
- City ICT CTO
- ICT Change Management
- City Cyber Security
Processes
- Asset Management Process
- Change Management Process
- Problem Management Process
- Quality Management Process
- Security Incident Management Process
- Security Monitoring Process
- Audit Process
Trigger Events
- New Asset Configuration Item
- Request for Change
- Security Incident
- Asset End of Life
- Audit
Key Inputs
- New Asset
- Change Request
- Audit Request
- Service Improvement
Key Outputs
- Asset Logging
- Asset Security Monitoring
- Audit Report
- Service Reports
Interfaces
- All Departments with Asset Management
- City Executive
- City Cyber Security
Capability Model
Through the assessment of existing Asset Management functions across a City and knowledge of new IOT, Smart and Connected Services enough data should allow the modelling of different views and levels of detail of the projected capabilities. At the Strategic level, there are various ways of using the design and development of models to support subsequent steps and activities. Modelling provides the means to explore the various criteria and relationships Capabilities have. It allows scenarios to be explored and test thinking and hypothesis set out by objectives and targets.
the example below is very simple and just an example. At some point I will provide additional ontological models to improve the definition of the Capability.
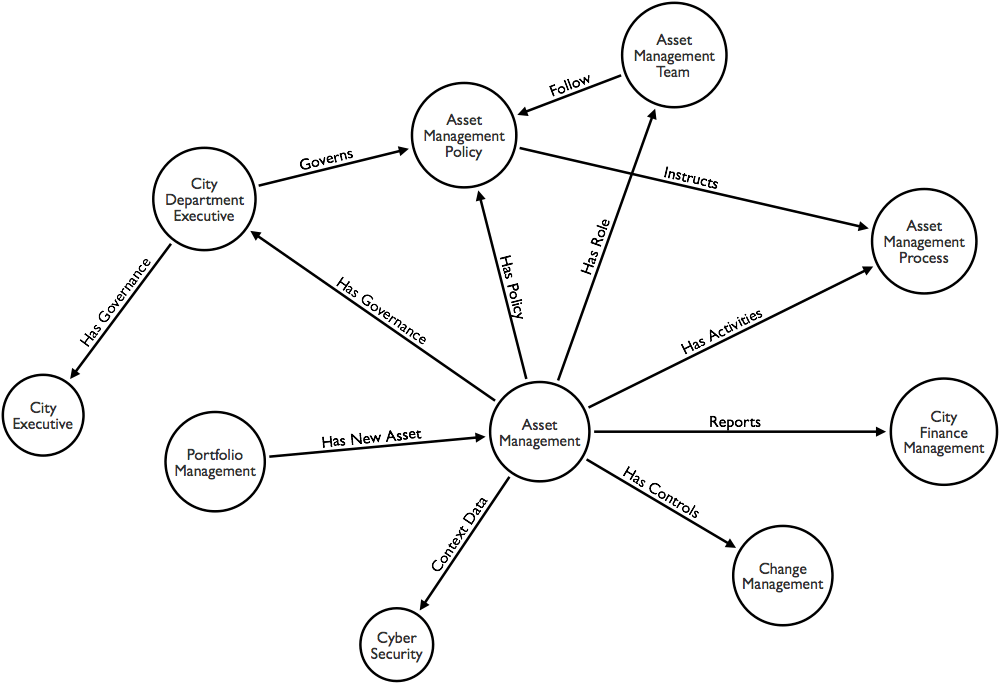
Roles and Responsibilities
Roles and Responsibilities should be assigned to single or multiple Actors. The Table below shows a simple matrix model which aligns Roles to Actors via a RACI and Frequency. The Frequency is defined to help address the work commitments over specific periods of time and manage the capacity of the Role.
| Activity / Role | Govern Capability | Govern Policy | Maintain Assets | Audit Assets |
|---|---|---|---|---|
| Executive | Accountable | Informed | Informed | Informed |
| Director | Responsible | Informed | Informed | Consulted |
| Asset Manager | Informed | Accountable | Accountable | Accountable |
| Asset Audit | Informed | Informed | Informed | Responsible |
| Asset Configuration | Informed | Informed | Responsible | Informed |
| Maintenance | Informed | Informed | Responsible | Informed |
| Frequency | A | Q | D | Q |
Solution and Technologies
Technologies and the data they consume or produce are integral within the role and objectives of a capability. The particular functional and non-functional requirements (service management) should be considered if the strategic option is to use a new technology solution.
| Functional Requirements | Asset Management Capability |
|---|---|
| Technology Platform | Yes |
| Technology Component | No |
| Storage | Yes |
| Communications | Yes |
| Interfaces | Yes |
| Reporting | Yes |
| Data Management | Yes |
| Authentication | Yes |
| Dashboards | Yes |
Service Management Requirements
Non-Functional Requirements | Asset Management Capability |
|---|---|
| Performance | Yes |
| Scalability | Yes |
| Capacity | No |
| Availability | Yes |
| Recoverability | Yes |
| Maintainability | Yes |
| Serviceability | Yes |
| Security | Yes |
| Regulatory | Yes |
| Manageability | Yes |
| Data Integrity | Yes |
| Interoperability | Yes |
Service Model
The service model and service criteria represent the means for a capability to exist and fulfil its objectives and obligations to the stakeholders it serves. The resources and technologies may be fulfilled by in-house resourcing or by externally contracted providers.
Service Model Criteria | Asset Management Capability |
|---|---|
| Metric – KPIs | Yes |
| Metric – PIs | Yes |
| Security Metric | Yes |
| Service Level Agreement | Yes |
| Service Report | Yes |
| Service Catalogue | Yes |
| Professional Services | No |
| Auditable | Yes |
| Service Threshold / Service Penalty | Yes |
| Maturity / Improvement | Yes |
| Service Cost Model | Yes |
Target Operating Model
The operating model is a key tool in the delivery of the Smart City Cyber Security Strategy. Understanding the elements of an operating model, their particular attributes and contribution as well as the integration of these elements is part of the critical path. These include the structure, accountability, behaviours, role decision rights, performance management and management processes that are needed to ensure effective resource planning and derived value. As a dependency, Asset Management as a single contributor or through each of the Departments should be included as a key capability.
Transformation Planning
Conditions
Define a set of strategic principles as the general guidelines to meet the cyber security scope of the Smart City Strategy. Build a set of high-level City Cyber Security requirements to set out the goals of the strategy to fit within the existing functional structure and requirement for any new functions.
Assessment
Conduct audits and appraisals of the current or As-Is situation to build up a baseline of the Smart City Current Operating Model. Further research and the identification of specific reference data will provide evidence of current working practices. Analyse the current operating model, references and evidence by undergoing a Gap Analysis project to highlight gaps, deficiency and problems.
Design
Using the Strategy as guidance and the findings made during the assessments and analysis to define the Target Operating Model to fit the vision and goals of the Smart City for Cyber Security. Test the Target Operating Model with scenarios and options as well as dependencies and assumptions. Once a more optimal model is defined this should be enhanced with benefits and justifications or business cases for further extensions.
Roadmap
A Cyber Security Strategy may require considerable changes across the Smart City. Break the Target Operating Model into main components that can be further broken down in the project plans and a critical path. This should be fully supported by an agreed delivery methodology. Define the transformation plan and roadmap to direct the changes and transitions and support all transformational work with necessary communication and reporting.
Performance, Change and Maturity
Cyber Security capabilities are no different to other organisation capabilities and thus require Performance Management to ensure service and execution performs to expected thresholds and targets. Key performance measures include Mean time to Detect, Mean time to Respond and Mean time to Recover.
Change is inevitable and must be anticipated as part of the Strategy as well as in-life during execution. Change will take place across the city as all cities will develop new systems, and services and as a consequence the cyber security capabilities must absorb this and readjust to whatever new variety that entails. More significantly is the change to the threat landscape as new threats emerge or older ones adapt to flaws or security changes that prevent there use. Again, Cyber Security capabilities cannot afford not to assess and adjust to this change through either resources, process or technology.
Adopting a Maturity Model and the corresponding assessment and
certification is an important way to determine how a capability is progressing in its development. A new cyber security capability will
take time for certain aspects to become fully effective. There is a
critical path and dependency basis for certain key capabilities and
more advanced ones may take longer to establish as they depend
upon the maturity of others before they can perform their roles.

