By adopting the NIST Cyber Security Framework as the guide to cyber security the next step is to integrate informative references applicable to the scope of the requirements per NIST Category. These informative references help to determine the depth of detail and the formation of policy and guidelines. Some categories will require some adjustment as well as the means to provide an in-depth assessment of legacy solutions and services as they integrate or transition into newer and IOT based / smart solutions. NIST Cyber Security Framework was not specifically designed for Smart Cities but organisations with predominately ICT and in some cases ICS systems. Whilst a good proportion of the framework is very valid, it does need extending to account for the nature and structure of a City and how it goes about a Smart transformation.
To help define the means to build and apply a framework I am going to borrow from a great example which is the book by David C Hay – Enterprise Model Patterns. It offers a generic model that is divided up into 5 key upper concepts:
- Parties – People and Organisation (Who)
- Geographic Locations (Where)
- Assets (What)
- Activities (How)
- Timing (When)
Using this will allow me to define the particular characteristics of a Smart City to map to the different types of requirements within NIST CSF. To describe the way of using NIST CSF and extending it, to support the differences a Smart City exhibit, I will use TOGAF and ISO 11179. These will help to build an architectural high-level view of smart services and technologies and the controls over the new concepts and domains they create. This will then help to model security threats and mitigations.
[It may be worth noting at this point that another useful reference would be the ISO 15926 standard which was developed for Industrial Automation Systems and the approach taken in their Data Model. In particular Parts 7 and 8 and the the Composition of Asset as a whole and its parts. i will come back to this at a later stage.]
The ISO/IEC 11179 model is a result of two principles of semantic theory, combined with basic principles of data modelling.
The first principle from semantic theory is the thesaurus type relation between wider and more narrow (or specific) concepts, e.g. the wide concept “income” has a relation to the more narrow concept “net income”.
The second principle from semantic theory is the relation between a concept and its representation, e.g., “buy” and “purchase” are the same concept although different terms are used. Source Wikipedia
The model that defines ISO 11179 is as per the table below.
|
Data Element Concept (DEC) – expressing 0..* DE – specifying 1..1 CD |
Conceptual Domain (CD) – representing 0..* VD – having 0..* DEC |
|
Data Element (DE) – expressed by 1..1 DEC – representing 1..1 VD |
Value Domain (VD) – represented by 1..1 CD – represented by 1..1 DE |
To give an example of this…
|
TOGAF: Business Service |
City Car Park |
|
TOGAF: Physical Technology Component |
Parking Sensor |
|
Data Element Concept |
Parking Service |
|
Data Element |
Parking Space |
|
Conceptual Domain |
Vehicle Parking Availability |
|
Value Domain |
Space Free / Used |
There are a number of supporting standards and guidelines for the development of smart cities including those from ETSI, OneM2M, IOTone and the NIST Smart Cities and Communities Framework Series (SCCF) etc which I will cross reference for supporting guidance. I will use each of the NIST CSF Functions and Subcategories to highlight areas where Smart City Cyber Security and Security Operations strategies need to address.
Finally i will outline how the mitigation use cases in each NIST CSF category help to address different parts of a threat’s context.
|
Threat Timing |
When |
Seasonal, Copy cat, Trends |
Associated with situational awareness so that key events both locally and globally can be monitored in case of increasing likelihood of threat. |
|
Threat Target |
Where & What |
People, Process, Technology |
Understanding of the focus of intent e.g. a key asset, and that asset’s role or purpose in a system. |
|
Mitre Att&ck Stage |
How |
Initial Access, Persistence, Exfiltration |
Each threat and attack is associated with a means to execute a particular technique in order to achieve an objective |
|
Threat Type |
What |
Spoofing, Disclosure, DoS |
The tools or tactic used in the execution of the attack |
|
Threat Level |
What |
Basic, High, APT |
The level of skill and dedication behind the attack |
|
Threat Motive |
Why |
Financial, Chaos, Espionage |
The reason and motivation for the attack |
Below is the diagram, used in a previous post, which addresses the complexity of task as a whole but also shows the need for this to be broken down into understandable, achievable and manageable parts.
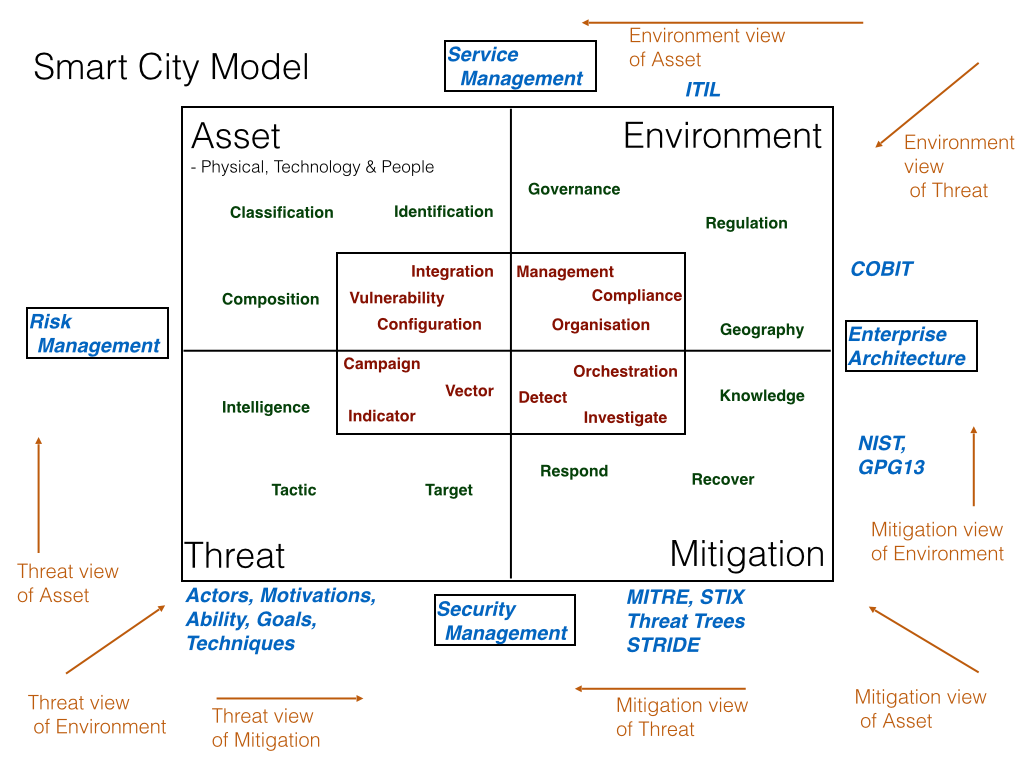
Below is the Function and Category sections of NIST CSF that will link to dedicated posts and resources associated with each category.
Identify
| Business Environment (ID.BE) |
| Governance (ID.GV) |
| Risk Assessment (ID.RA) |
| Risk Management Strategy (ID.RM) |
| Supply Chain Risk Management (ID.SC) |
Protect
| Identity Management, Authentication and Access Control (PR.AC) |
| Awareness and Training (PR.AT) |
| Data Security (PR.DS) |
| Information Protection Processes and Procedures (PR.IP) |
|
Maintenance (PR.MA) |
|
Protective Technology (PR.PT) |
Detect
| Anomalies and Events (DE.AE) |
| Security Continuous Monitoring (DE.CM) |
| Detection Processes (DE.DP) |
Respond
|
Response Planning (RS.RP) |
|
Communications (RS.CO) |
| Analysis (RS.AN) |
| Mitigation (RS.MI) |
| Improvements (RS.IM) |
Recover
| Recovery Planning (RC.RP) |
| Improvements (RC.IM) |
| Communications (RC.CO) |
